| University | Teesside University (TU) |
| Subject | Ethical Hacking |
Scenario
A not-for-profit organisation working in the area of protection of human rights asks you to plan, execute, and document an ethical hack against their systems in order to assess their security. Moreover, based on your findings, you are required to provide advice on how to improve the security of the system.
The organization periodically receives confidential reports from correspondents and advisors regarding the alleged violation of human rights. These reports can be the bases for actions taken by the organisation such as providing legal support, launch urgent actions, sending information to supranational institutions like for example the “United Nations Human Rights Office for the High Commissioner”. An example of the nature of such communications can be found here: https://www.ohchr.org/EN/Issues/Housing/Pages/IndividualComplaints.aspx
The organisation is concerned that a possible data breaches that may compromise the confidentiality of the information and the identity of correspondents and advisors.
For the purpose of your security analysis, they provide you the following scheme and details:
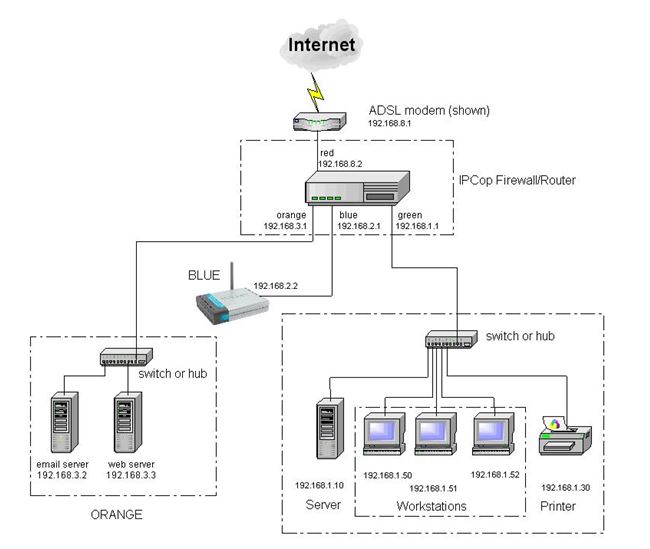
IPCop is a Linux based firewall/router that controls the access to different zones of the system (zones can be seen as separate network entities, with no traffic across zones allowed without special permission):
Red — the Internet
Green — the safe zone for maximum protection
Orange — a DMZ designed for Web, mail, or other Internet servers
Blue — for wireless networks
Hire a Professional Essay & Assignment Writer for completing your Academic Assessments
Native Singapore Writers Team
- 100% Plagiarism-Free Essay
- Highest Satisfaction Rate
- Free Revision
- On-Time Delivery
Orange Zone:
The webserver is an Ubuntu 16.04 LTS machine running Apache 2.4.x
The email server is an MS Windows Server 2012R2, running MailEnable Standard Edition 10.26
Green Zone:
The Server: Windows 2012R2, with Active Directory, DHCP, DNS, IIS. The server also runs a MySQL Server 5.5, the back-end for a custom web application that is used by the financial office. The server contains also shared folders, which are used for different purposes: projects, advisors reports, and other classified and non-classified documents. The workstations are Windows 10.
Blue Zone:
Employees and volunteers are allowed to bring their own devices and connect to the internet.
No further information and no credentials are given except the public IP address and the domain name of the webserver (since this information is purely hypothetical we simply use these placeholders <PUBLIC_IP_ADDRESS> and <DOMAIN_NAME> to indicate them in your report).
The client specifically requests that:
- No data should be lost from any system during the pen-testing. If any change is done, for a proof-of-concept, you should also identify a procedure to restore the system to the previous state;
- The risk of disrupting the services should be minimised, in particular during office hours;
- You have a limited number of hours for this task, so your planning should prioritise the key services and components;
- The pen testing activities should be carried out with FOSS or free software unless such an option does not exist for a specific task. In this case, you should make clear the license terms and costs.
Task
You should write a report (approximately 4500 words, submitted in PDF format) detailing your plan, with a justification for tools and techniques used, the results, and a complete chronological audit trail of hacking actions taken in line with expected professional and ethical standards.
In particular, for the practical part, you have to carry out a pen testing limited to a given component. For the rest of the work, use the information provided in the scenario, and make the appropriate reasonable assumptions if necessary (provide a rationale for it).
The report will have cover all the stages of the ethical hacking methodology. The report should include at least the following elements (xx% indicates the weight in the mark allocation):
- Demonstration of understanding of the scenario and discussion of the pre-engagement interactions.
- Identification of relevant tools for each stage of ethical hacking.
- Appropriate information gathering and threat modeling
- Identification of security vulnerabilities
- The exploitation of the vulnerabilities
- Post exploitation activities
- Reporting of the findings and potential suggestions for countermeasures
- Critical reflection of self-performance and the development of skills for employment as a computer security professional.
We at SingaporeAssignmentHelp.com offer ethical hacking assignment help services to Teesside University scholars by our online assignment experts. Our experts help the students in making a high-quality information technology assignment document and help them to grab high grades in their academics.
Looking for Plagiarism free Answers for your college/ university Assignments.
- ANL303 Data Analysis of Diabetes: Exploring K-Means and Apriori Models for Patient Profiling, GBA
- HRM335 Exploring Leadership Adaptability: Insights from Industry Leaders (GBA)
- ELG101 Linguistic Analysis of Affixes, Word Formation, Syntax, and Social Media’s Impact on Language (TMA02)
- MTH355 Solving Linear Equations and Optimization Using LU Decomposition and Linear Programming, TMA
- PSY352 Cultural Evolution And Persistence in a Changing World, ECA
- CMM315 The Rwandan Genocide and Peacebuilding Efforts, ECA
- HRM335 Reflecting on Leadership Experiences: Connecting Theory to Practice (TMA02)
- MGT568 Agile Leadership in CEO Succession Planning: Strategies for Organisational Success (ECA)
- MGT568 Agile Leadership Scenario Planning: Strategies for Business Resilience
- GSP165 Legal Principles in Divorce, Child Custody & Estate Distribution

